As if ransomware and viruses weren’t enough of a threat already from all those dark web overlords, a new and more covert threat has emerged onto the scene causing a substantial amount of damage to businesses and individuals the world over. The worst of it is that it is, for the most part, not even illegal and very hard to detect.
While we are all familiar with the concept of mining, when it comes to mining crypto currency we may be a little less clued up. In brief, there are people out there who dedicate vast amounts of time and resources into mining crypto currencies like Bitcoin, Dash, Ethereum and Litecoin, to name but a few. What these miners do is have their computers solve a bunch of complicated algorithms which, once solved, unlock crypto coins which are then added to the currency pool.
Unfortunately, because these mining activities use up so much computer power and resources, miners are often on the lookout for unsuspecting people to “cryptojack” in order to use their computer resources for mining. Basically what happens is that your technology gets hacked and used as a mining “pickaxe,” as it were, to mine more crypto coins. This slows down your computer or device and even leads to it shutting down for no reason at times.
Any device that is linked to the internet can be used as a “pickaxe” for these miners.
And the more devices they have in their arsenal, the more they can mine and the bigger return they receive. Whilst there is nothing illegal about cryptomining, when the person doing the mining decides to use your devices without your permission to aid in their mining it is then that it becomes illegal.
Norton Antivirus has cryptomining software programmed into their antivirus software so that when you activate it you are allowing them to use your device to mine crypto coins and even earn a percentage of whatever you mine as well as charging a fee for transferring the currency you mine to a different wallet.
However, they do require that you have a specific type of graphics card as well as at least 6GB of memory on your device. Added to this you will have to activate the mining software by clicking on the button that asks you if you want to turn your computer’s idle time into cash, so it doesn’t activate of and by itself, therefore it is not illegal as it needs your permission before it gets to work. But think about the cost of the wear and tear on your device versus the promised payout.
At the end of the day, though, not all crypto-miners are that considerate. All too often they will hack your device by going through an app you installed and will use your technology without your permission.
These maliciously malodorous crooks are called crypto-jackers. These days, cryptojacking is becoming ever more popular among cyber criminals as they can earn an income simply by using resources that they don’t own and which they don’t need to pay for, the use of which they obtain illegally through malware implanted on your device.
Are You A Victim of Cryptojacking?
So how do you know whether or not you’ve fallen victim to a crypto-jacker? First things first, you could check to see if your CPU (Central Processing Unit) resources are being maxed to the limit. To do this, you can simultaneously press down on the ALT, CTRL and Delete buttons on your keyboard — this will open up your task manager.
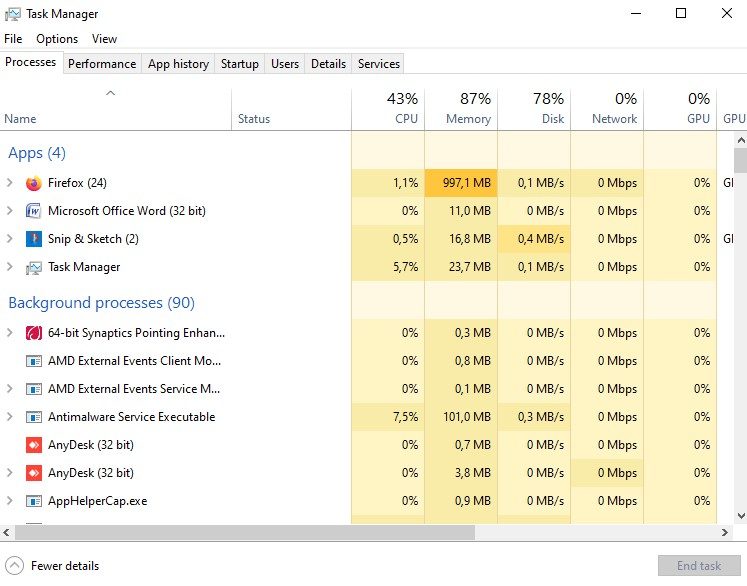
Alternatively, you can also press the Windows key, and then type in Task Manager and left-click on the application. Once it is open you will be able to see the status of your CPU by looking at the CPU column.
If it is running at ninety percent or more and the program that is using all of that power is not one you recognize or actually use, there may definitely be something fishy going on.
Something else you could check is to see whether or not your internet browser carries on running in the background once you have closed down. To check that you will need to close your browser by left-clicking on the little X in the top right-hand corner of your screen.
Once you have closed it you can open up the Task Manager again and see whether or not it still shows as running. If it is still running then it means that your browser is still consuming your computer resources.
Another clue that your device may have been hacked by a crypto-miner is if it overheats regularly or continuously and if your battery drains (goes flat) faster than usual. These are generally signs that your device is using enormous amounts of power and this can have detrimental effects in the long term.
Many hackers use innocuous looking apps to hide their cryptomining malware and so you can quite inadvertently install malicious malware that will set you up for disaster … and some potentially high electricity and/or internet bills.
Can You Remedy It?
In order to prevent your device from being hijacked by these crypto crooks, you need to make sure that you keep your device completely up to date with the latest software upgrades.
To check for the latest upgrade on your mobile device, navigate to Settings (usually by swiping down from the top of the screen) and then scrolling down to where it says System or System Update or even Software Update, depending on which device you have.
Before you tap on it, make sure that you are connected to the Wi-Fi as it will need to download the latest version if you are not currently running the latest software version. If there is a new update which needs to be installed, simply tap on it and allow your phone to install the update.
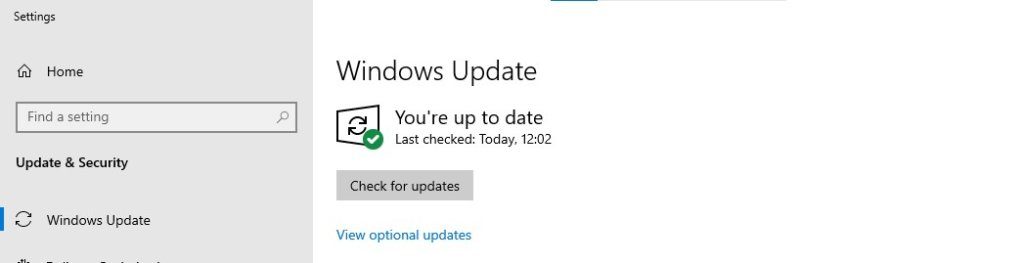
To check if you are running the latest software version on your laptop or tablet, press the Windows key and type in Windows Update. Now left-click on the button that says Check for Updates and if you are running the latest update then it will tell you so, otherwise it will advise you that there is a new update and ask you if you want to install it.
You can also limit the opportunities for hackers to get in unannounced by only installing trusted applications from the Google Play Store or the Apple Store. Check the ratings of the apps you want to install as well as the amount of times the program has been installed.
Remember to listen to your gut — if you get a feeling that something may be a little fishy, steer clear of it! As added protection against these hackers, install some antivirus software to regularly scan for threats.
Something else you can do to guard against cryptojacking is to install an anti-malware program which can be used to scan for any malicious or malignant malware that you may have inadvertently picked up or installed when you installed that game of Solitaire you enjoy playing or downloaded that latest news report the other day.
By doing regular scans (perhaps on a weekly basis) you will be able to pick up sooner rather than later if there is anything concerning on your computer or device.
It might sound to some as though this cryptojacking isn’t as bad as all that, but for others it is a sad and devastating reality. Not only can it cause your device to overheat or restart, but the end result is that it can cause the battery to expand and swell and cause permanent damage and malfunction, leading to you needing to replace your device.
A word to the wise … it’s best to take adequate precautions before so that you don’t need to deal with the disasters that follow. Don’t install applications from unknown sources, and even when downloading from the Play Store, make sure that you thoroughly check to see whether or not the app is safe.
Apple has incredibly high security and so the chances of having crypto-jackers hijack your device is minimal, but whilst Google operating systems are more vulnerable, they have taken a page out of Apple’s playbook and have made a point of informing developers that they will no longer accept the mining of crypto currencies on their devices.
Be extra vigilant when using the internet or browsing through web pages. Only open emails and attachments from trusted sources and keep your computer security up to date by using two-step authentication and smart passwords.
Overall, the best thing to do is to make sure that you are constantly on the lookout and are tuned in to any changes to your devices. That way, if something does happen, you will be able to catch it right at the start before too much damage has been done. If they’re working harder than they used to all of a sudden, something is definitely wrong.
As always, if you’re needing any kind of additional help either understanding or implementing any of the advice mentioned in this article, consider reaching out to HelpCloud technicians for remote support.