Fake email, also known as spoofed email, is email sent by unknown, often malicious, third parties that is disguised so it appears to come from a trusted source, such as a reputable company, a business associate or family and friends from your contacts list.
Fake email is used to deliver spam messages, viruses and other malware, or phishing links and attachments that trick the recipient into disclosing personal or sensitive information that can then be used to commit fraud or attack other legitimate Internet users.
According to a study by IBM, spam email increased fourfold in 2016 and Symantec reports fake email now accounts for 50% of all email traffic on the Internet.
Email remains the most popular method for spammers and cybercriminals to deliver malware and Symantec reports 1 in every 131 emails sent in 2016 contained malware.
Internet service providers, online security companies and web site hosting companies deploy a wide range of methods to try to block fake and dangerous email from ever reaching your inbox. If these measures are defeated, anti-virus and anti-malware companies provide software products you can use to scan and remove or protect against malicious email as it enters and leaves your computer. However, a great deal of fake email still gets through and some of it is so convincing that many victims are tricked.
There are extra steps you can take and some common sense habits you can adopt that can protect you and the people you communicate with via email. It may take a little longer to follow these steps, but the time spent will be insignificant compared to the potential damage should you inadvertently download malicious software, or spread a virus to your entire contact list, or disclose information that leads to a financial loss, identity theft or other harmful consequences.
If you feel that you are vulnerable and are not savvy enough to keep yourself protected while emailing or browsing the internet then consider a membership with HelpCloud Tech Support. There’s great value in having go-to experts available 24/7. Additionally, the membership includes the best in antivirus and firewall services: Webroot SecureAnywhere.
Email Information is Easy to Fake and Disguise
First and foremost, understand it is very easy to fake the information contained in an email. Don’t trust the From field, this is easy to spoof. Just because the email appears to come from a trusted source doesn’t make it so. A favourite trick of spammers and cybercriminals is to change the email sender so it appears to come from a bank or a popular online company such as Amazon or a well known courier firm.
Subject lines are also used to trick recipients. Symantec reported the number one subject line relates to fake invoices, often accompanied by an attachment that pretends to contain the invoice.
Links contained in fake email will often lead to compromised web sites that contain malware or are disguised to look like legitimate sites. It is very easy to copy entire web sites and fool visitors into thinking they are interacting with the real thing. Particularly dangerous are login forms on fake web sites that can steal your credentials for the real web site.
If you are not expecting the email, for example if you receive email that includes an invoice for a product or service you never ordered, or details delivery instructions for a package you know nothing about, the high probability is the email is fake. When was the last time you accidentally received a free laptop computer or booked flight tickets to an expensive destination? Common sense tells you it’s fake. But curiosity and desire can get the better of you if you aren’t careful.
For links contained within email, don’t click right away. Instead hover your mouse over the link and your email client will likely display the underlying URL (or web site address) the link points to. If the email supposedly comes from a well known company but the link URL points to a strange address that has nothing to do with that company, you are almost certainly dealing with fake email.
Sometimes the link URL will be more sophisticated and, without careful inspection, can appear to point to a legitimate source. The web address might be almost identical to the real thing apart from a single letter being swapped around or a number used to substitute a letter. For example, Amazon will always send email from a legitimate domain such as amazon.com, or amazon.co.uk. A spammer might acquire the domain amezon.com, or amazom.com and a quick glance might not spot the difference.
Check links carefully before you click. Better yet, and using the example of Amazon again, if an email claims to be in some way related to your account then go directly to the web site instead of clicking the link in the email. If you really have a package waiting, or if you genuinely need to make a payment then the details will be available on the web site and you can conduct your business securely there.
Almost all legitimate companies now use SSL/ TLS. This means their links will begin with https:// rather than http:// and indicates all communication between your computer and their web site is encrypted. This isn’t a 100% guarantee, as spammers can buy SSL certificates too, but a bank or an online store will never conduct transactions over an non-encrypted link so if you see these links in your email you should be suspicious.
Banks and online stores will never send you email asking for you login details or other sensitive information. If you see such a request, for example if you get a message warning your your account has been hacked and asking you to follow a link to change your password, be very careful. This is likely a fake. Even worse, if the email provides a telephone number for you to call and you are then asked for a password, hang up. Go to the legitimate company web site, find the real contact details and phone if you are concerned.
The golden rule, never, ever give out personal information via email or via a link your have followed from an email. Instead, read the email and contact the company directly.
Check for Telltale Signs
When trying to determine if an email is the real thing or a spoof, read through the content and look for spelling and grammar mistakes. Professional companies rarely make these errors. Some of the less sophisticated spammers and fraudsters who don’t have English as their first language often make mistakes that are easy to spot.
Watch out for frightening or agressive subject lines that demand you take action instantly or suffer dire consequences. Subject lines such as, “Your account has been hacked!”, will never be used by legitimate companies.
Check for strange or uncommon greetings that are personalised or contain odd words or codes. For example, “My dear friend john”, is not likely to be sent by your bank. Notice “john” is in lower case. Or even more obvious, “Greetings {USERNAME}”, where software being used by the spammer hasn’t been set up correctly.
Spammers like to send bulk mail, sometimes millions of emails in a short space of time. And spam outbreaks are often the work of multiple spammers. So if you see a suspicious mail, wait a while. Chances are an identical or almost identical copy will pop into your inbox. Or you’ll be inundated with multiple copies as more and more spammers get in on the act. Delete them all.
Check the Email Source Code
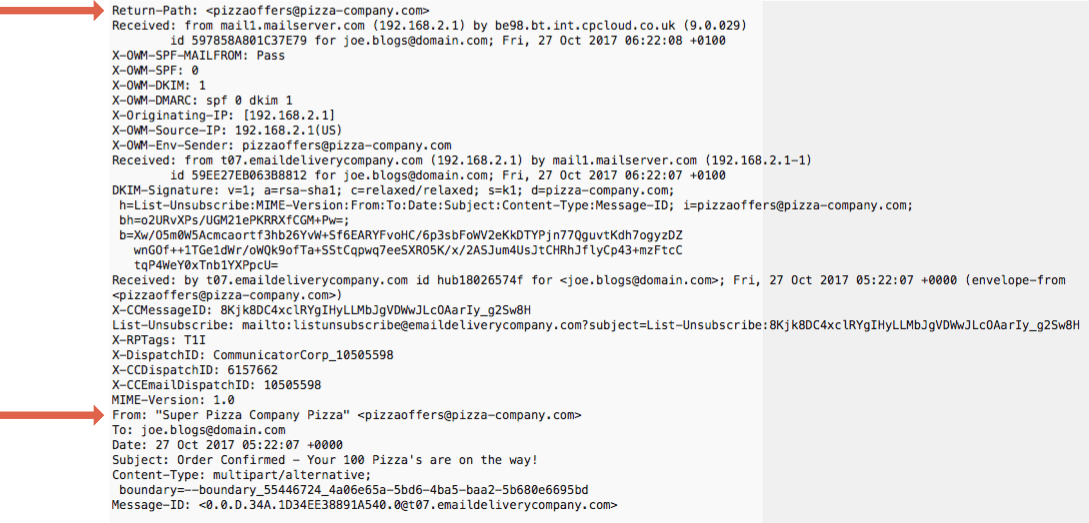
This is a little tricker for non-technical users, but the email source code can provide valuable and conclusive information that will help you spot fakes.
Email in its most basic form is just a text message. This text contains not just the words in the email message you can see, but also a header that contains further information about the message such as who sent it, how it was delivered and whether is has passed the various spam tests it encountered along the delivery route.
The email header contains the fields you are familiar with, such as From, CC, BCC and the subject line. These are all easy to fake. However, the email header will also contain a return path. The return path is the email address replies will be sent to and it is much harder to fake than the From field.
Your email client software or web browser, if you are using a webmail account, will have an option to view the email or message source. Or it should at least have an option to examine the email header. Use this option to examine the underlying email header. You’ll likely see a whole stream of indecipherable text, but somewhere in there (at or near the top) look for text that refers to the return-path and check the email address it relates to.
Now scan down and look for the From: address. Do the return path and from address both refer to the same mail domain? The addresses may not be identical, but the segment after the @ symbol should match.
You can also take a quick scan through the header, even if it seems complicated, and look for any obviously problems. For example, if the email is supposed to come from a US company but you see references to domain names in Russia (.ru) or China (.cn), ask yourself, why would your email be travelling through servers in those countries?
If in Doubt, Don’t Click or Download
We receive many different types of email on a daily basis, most will be legitimate, some will be obvious spam, it’s only a few that might give us cause for concern.
If anything at all seems suspicious about an email, if it is unexpected, if it relates to something you know does not tally with your online activity such as an unexpected delivery, if it’s simply too good to be true – don’t click the links contained in the email, don’t download the attachments.
Instead, ring the company directly to verify the message. Or send an email to your friend asking for confirmation they just sent you a link to the latest funny video on Facebook.
Just a little bit of care an attention can prevent the irritating at best and possibly very serious consequences of spam, malware, phishing and other unwanted email based Internet scams and frauds.
If you feel that you are vulnerable and not savvy enough to keep yourself protected while emailing or browsing the internet then consider a membership with HelpCloud Tech Support. There’s great value in having go-to experts available 24/7. Additionally, the membership includes the best in antivirus and firewall services: Webroot SecureAnywhere.
